
GitHub abused to distribute payloads on behalf of malware-as-a-service
The repository offered the MaaS a distribution channel not blocked in many networks.


The repository offered the MaaS a distribution channel not blocked in many networks.

Overstep backdoor nukes key log entries, making detection hard.
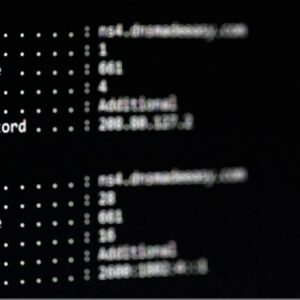
Technique transforms the Internet DNS into an unconventional file storage system.

GPUhammer is the first to flip bits in onboard GPU memory. It likely won't be the last.

Suspects were allegedly involved in a string of ransomware breaches.
Extensions load unknown sites into invisible Windows. What could go wrong?

Exploits allow hackers to bypass 2FA and commandeer vulnerable devices.

Important changes to Android devices took effect starting Monday.

Creators say app is intended for parental monitoring. So why the emphasis on stealth?

Move is aimed at curbing a form of abuse that costs subscribers dearly.

Agencies warn that some US targets may be needlessly exposed.

Official was connected to FBI probe of cartel kingpin Joaquín “El Chapo” Guzmán.

AMI MegaRAC used in servers from AMD, ARM, Fujitsu, Gigabyte, and Qualcomm.

Overtime defenses for Spectre-based attacks have taken their toll.

Maximum-security Cisco vulnerability was patched Oct. 2023 and exploited Feb. 2025.

Attacker rained down the equivalent of 9,300 full-length HD movies in just 45 seconds.

Microsoft, Apple, Bank of America, and many more sites all targeted.

Provisions on secure software, quantum–resistant crypto, and more are scrapped.

The soaring price of copper makes networks tempting targets for thieves.

Apple OSes will soon transfer passkeys seamlessly and securely across platforms.

The publicly available exploits provide a near-universal way to bypass key protections.

BadBox malware has been menacing low-cost Android devices for nearly a decade.

Chunghwa Telecom and Netlock customers must look elsewhere for new certificates.
Abuse allows Meta and Yandex to attach persistent identifiers to detailed browsing histories.

Backdoor giving full administrative control can survive reboots and firmware updates.

AI assistants can't be trusted to produce safe code.

Payloads were set to spontaneously detonate on specific dates with no warning.

Even after its refurbishing, Recall provides few ways to exclude specific apps.

For the first time, new quantum-safe algorithms can be invoked using standard Windows APIs.

Warning comes as the use of deepfakes in the wild is rising.

Attacks spilled contacts and emails from targeted accounts.

A single flip of a settings button enables a host of defenses against hacking.

Malicious "context manipulation" technique causes bot to send payments to attacker's wallet.

The presence of credentials in leaked "stealer logs" indicates his device was infected.

The verdict is a major victory for opponents of exploit sellers.